Xenonauts 2
- Genres
- Strategy, Simulators, Steam
- Release date:
- 18/07/2023
- Publisher:
- Hooded Horse
- Developer:
- Goldhawk Interactive
- Localization:
- EN
Note: This Early Access game is not complete and may or may not change further.
Xenonauts 2 is a strategy game that puts you in charge of a multinational military organization tasked with eliminating an extraterrestrial threat. Working from the shadows, you must seek out and engage the growing alien presence wherever it appears. Expand and manage a covert network of bases across the globe. Pursue research and development to bridge the technological gap with the alien invaders. Train, arm, and command your ground troops wherever the alien threat emerges.
THE ENEMY IS EVERYWHERE
It is 2009 - the Cold War continues, and the Berlin Wall still stands. In the shadows, a secret organization works beyond arbitrary political boundaries to gather information about a greater threat to humanity. Mysterious sightings of unidentified flying objects and unknown beings have grown more common, coinciding with escalating international tensions and panic. Those who report such sightings frequently disappear without a trace, and it is clear that the aliens grow bolder with each passing day. Time is of the essence.

A MYSTERIOUS THREAT
Knowledge is power - unfortunately, little is known about the alien menace when you take charge. You will need to engage in combat operations around the globe to learn what you're up against. Eliminate extraterrestrial forces in deadly tactical battles to recover research samples, allowing your scientists to improve your equipment and slowly uncover the truth about the alien invasion.
- A massive variety of enemy types will keep you on your toes as you fight against a multitude of species, each with their own strengths, weaknesses, and fighting styles. Securing alien bodies to perform autopsies on will give you insights into their potential weaknesses, allowing you to prepare accordingly.
- Aliens aren't all you'll be fighting - human agents known as Cleaners work in tandem with the extraterrestrial threat, bringing with them added varieties of troops, combat locations, and mission objectives. The Cleaners work to further alien goals and objectives, operating directly under their influence - any strike against the Cleaners is an indirect strike against their alien overlords. You will have the opportunity to gather intel by infiltrating their bases, securing data, and seeing how far the conspiracy goes.
- Every combat engagement is an opportunity to learn more about the enemy force and how it fights - if you're willing to take the risk. Will you look to quickly eliminate active threats using explosives, grenades, and missiles, or will you take a more tempered approach to secure bodies and alien technology that can be taken back to HQ for autopsies and reverse-engineering? Will you focus on the development of airpower to bring down UFOs and investigate their crash sites for additional intel? Your adversary has the advantage in both technology and equipment – any choice you make will involve tradeoffs.
IN-DEPTH STRATEGIC LAYER
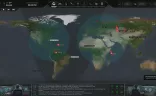
The war against the alien force takes on a global scale - as they attack indiscriminately, your troops must be prepared to operate across the globe using multiple bases, taking time between operations to rest, recuperate, rearm, research, and eventually reengage the enemy. No two campaigns are the same as complex simulations ensure even the smallest variances in decisions will have far-reaching impacts across the entire game.
- A small radar station in Alaska detects an anomaly over the Bering Strait. Air Bases in Kamchatka and Yukon scramble jets to investigate, chasing multiple bogeys each, bringing them down over the water. Thousands of miles away, a radar station in Italy works in tandem with response teams stationed at a base in Algeria and an air base in France to take down alien operations on the Iberian Peninsula. Meanwhile, a new base is being built in Southeast Asia where the invaders have slipped through the cracks multiple times, inciting panic. Build, design, and manage multiple bases, each with its own squadrons of fighter jets and transports, radar arrays, research teams, operatives, and more. Consider the limitations of fuel ranges when you place them and use a grid-based construction system to optimally lay each of your bases out. Specialize your bases for detection, rapid response teams, research, manufacturing, and defenses as you see fit.
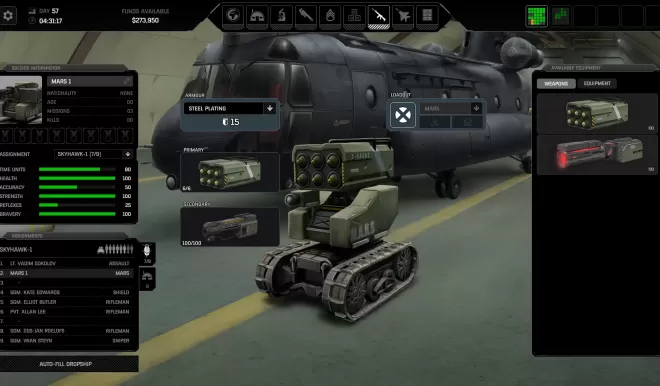
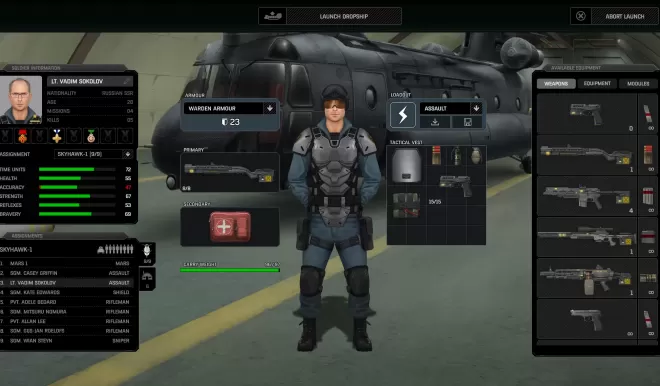
- Pursue multiple avenues of research to acquire a vast variety of aircraft, vehicles, weapons, armor, and other battlefield equipment to experiment with. Your approach on the battlefield will be determined by a combination the terrain you're engaging in and what equipment you've chosen to bring to the field. The presence of mechanized combat platforms and vehicles can tilt many situations in your favor as they break through cover and deliver particularly devastating ordnance, though their use can come at the cost of the ability to procure valuable resources from intact alien bodies and equipment. The research tree is vast, with over one hundred projects to unlock, allowing you to take on the alien threat with your own personal strategic and tactical touches.
- Infuse alien technology across all manner of equipment, and even develop autonomous battlefield combat platforms and sentry guns to assist with your forward operations as well as the defense of your bases. If you give your engineering teams enough time, money, and resources, you'll find yourself well equipped for the threat - unfortunately, all three are perpetually scarce. Will you rush to produce automated combat platforms to minimize the threat to your operatives? Or produce additional dropships to respond to more threats at a time? Or will you seek improved armaments for your fighters to strengthen their ability to intercept and take down alien squadrons?
- Training centers you build at your bases allow soldiers to improve their combat capabilities during downtime, but actual combat experience is of course of unparalleled value. Each mission gives your operatives an opportunity to improve their abilities according to the actual actions they take in combat, and even earn medals for their deeds.
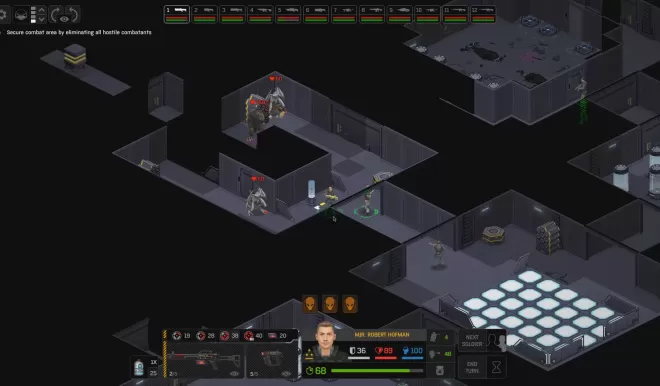
DEVASTATING TACTICAL COMBAT
Whether fighting in the air or on the ground, your tactical prowess is put to the test when engaging alien attackers. Battles are extremely dangerous affairs, asking you to manage positioning, ammunition, lines of sight, cover, and much more besides - many of your operatives will get wounded, and many of them will die, but those that survive grow more experienced and are more capable of taking on future dangers.
- Scramble jets to respond to UFO sightings, engaging them in real-time tactical battles that put you in command of your fighter wings. Tell your pilots how to maneuver and who to target, ensuring their victory while also keeping an eye on their fuel gauge and the proximity of your nearby hangers. No forced 1-1 duals here – if the aliens bring a technologically advanced and heavily armed space craft to the fight, gang up and send a whole squadron of your best planes to bring it down. The strategic layer and air battles are closely intertwined, and your careful planning of your global network of bases is of the utmost importance.
- Put boots on the ground by sending in your operatives for a variety of mission types, pursuing a range of objectives, but beware – your adversaries will not passively wait for you to discover them. Aliens will actively maneuver and seek you out from across the map, moving intelligently to strike at you from beyond visual range, hiding behind cover and taking advantage of the high ground. Maximize your chance of success through effective reconnaissance and lay ambush to eliminate the enemy.
- The battlefield is a dangerous place, and with an alien threat that will not stand idly by as you try to hunt them down, losses are inevitable. This isn’t the story of an elite squad of heroes winning battle after battle without loss – war is hell, and many of your troops will give their lives to resist the alien invasion. Your veteran troops will be invaluable, but even your basic recruits are skilled soldiers ready for combat. It is up to you to enable them to become the veterans of tomorrow.
Xenonauts 2 is a standalone title that does not need any experience playing the original Xenonauts to follow the story or enjoy the gameplay experience. The punishing battles, in-depth strategic layer, and complex simulations will take fans of the series and newcomers alike through a dark and deadly story about the defense of Earth and all humankind.
Trademarks, tradenames, and copyrights are property of their respective owners, Goldhawk Interactive (2023) and Hooded Horse Inc.™ (2023). All Rights Reserved.
System requirements:
MINIMUM:
- OS: Windows 10
- Processor: i5-4690 (or equivalent)
- Memory: 8 GB RAM
- Graphics: GTX 770 (or equivalent)
- DirectX: Version 12
- Storage: 6 GB available space
RECOMMENDED:
- OS: Windows 10
- Processor: i5-7600 (or equivalent)
- Memory: 16 GB RAM
- Graphics: GTX 970 (or equivalent)
- DirectX: Version 12
- Storage: 10 GB available space